Blog
US Federal Government Making Big Strides in DMARC Implementation
By Shehzad Mirza
On October 16th, the US Department of Homeland Security (DHS) issued Binding Operational Directive 18-01 (BOD 18-01) in which all federal agencies are mandated to implement various email security measures, one which of which is DMARC. Prior to its issuance, there was very slow progress. We are excited, however, in the large increase in DMARC implementation amongst federal agencies since the 16th!
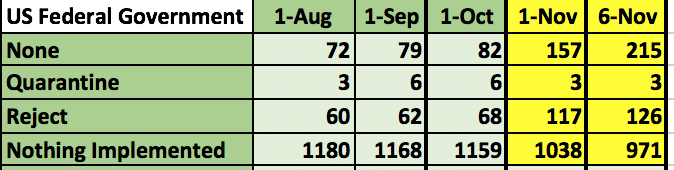
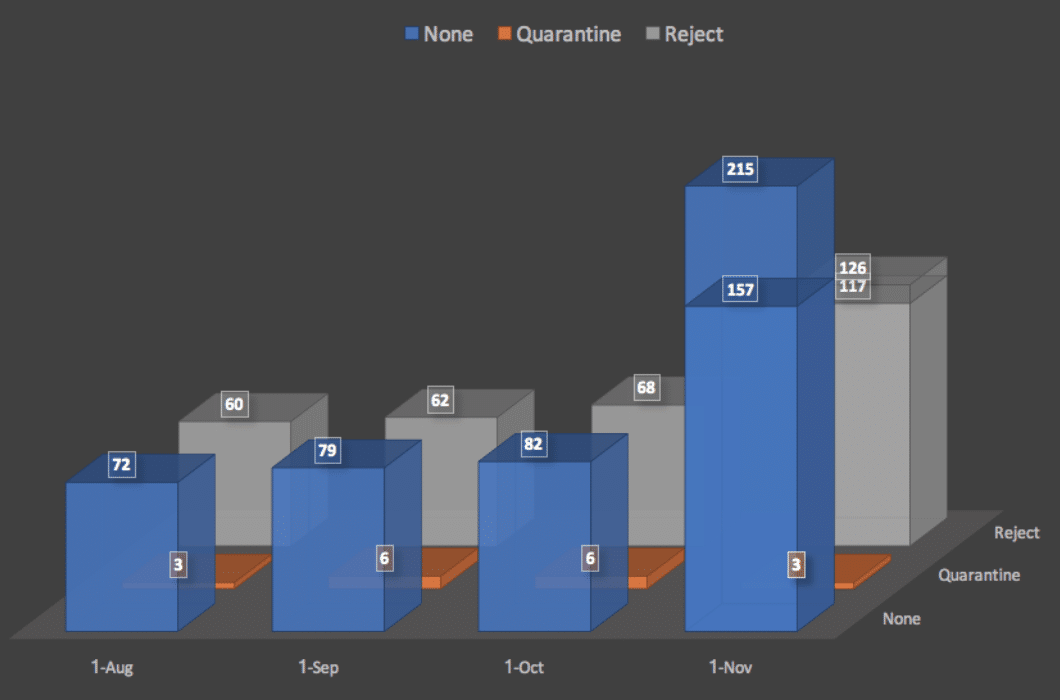 Figure 1: DMARC Implementation for federal domainsAt the beginning of October, there were 1,159 federal agencies without DMARC: 82 using policy level ‘none’, 6 using policy level ‘quarantine,’ and 68 using policy level ‘reject.’ On November 1st, the numbers were much better.
Figure 1: DMARC Implementation for federal domainsAt the beginning of October, there were 1,159 federal agencies without DMARC: 82 using policy level ‘none’, 6 using policy level ‘quarantine,’ and 68 using policy level ‘reject.’ On November 1st, the numbers were much better.
There are now 1,038 federal agencies without DMARC: 157 using policy level ‘none,’ 3 using policy level ‘quarantine,’ and 117 using policy level ‘reject.’ Just five days later, on November 6th, the number increased even more.
There are now 971 federal agencies without DMARC: 215 using policy level ‘none,’, 3 using policy level ‘quarantine,’ and 126 using policy level ‘reject.’
The number of domains using policy level ‘quarantine’ dropped but for good reason. Those three domains moved up to the highest DMARC policy level ‘reject.’
The increase in the number of domains at DMARC policy ‘reject’ is a big improvement. What is especially important about this increase is that 96 of those domains are not used for email purposes. This is based on the SPF record for those domains, which is set to “v=spf1 -all”. This means that there are no authorized systems to send on behalf of those domains. However, there are 137 additional federal domains that are using the same SPF record. For those domains, 108 domains should also implement a DMARC policy ‘reject’, assuming that they are not to be used for email. The remaining 29 domains are using the same SPF record, but the DMARC policy level is ‘none’. It is possible those agencies are either confirming that email is used for those domains or are in the process of adjusting the SPF records after reviewing the DMARC reports.
One area of minor concern is that nine of the agency domains that have implemented DMARC have done so without enabling reporting. Four of these domains are using DMARC level ‘none without reporting. DMARC level ‘none’ has no impact on messages and is meant only for monitoring purposes, but it is useless if the reporting is not enabled. The remaining five domains are using the DMARC policy level of ‘reject’ without reporting enabled. This is not a huge concern since they are at the highest level, but the reports can still be useful to IT staff for troubleshooting, and for cyber security staff to obtain cyber intel in the form of spammers/phishers.
The 215 federal domains that are at DMARC policy level ‘none’, must not forget to still keep working towards an effective DMARC policy of ‘quarantine’ or ‘reject’. Only at one of these levels will there be an impact on usage of their domain name.
There are still 68 days for the remaining 971 federal domains to implement a DMARC of policy ‘none’, and based on the pace of implementation so far, past few days, they should be able to make it. This is very encouraging compared to other sectors.
We strongly encourage everyone to follow the leadership of DHS and the United Kingdom government with the implementation of DMARC and to use our DMARC Setup Guide (which is now available in thirteen languages). We also have many resources (awareness videos and tutorials, monthly Webinars, and information resources) available to assist with DMARC implementation and ensure use of the reporting capability of DMARC. There is a lot of valuable information for an organization’s IT and security staff in those reports.
The author, Shehzad Mirza, is the Director of Operations at the Global Cyber Alliance. You can connect with Shehzad on LinkedIn.



