Blog
Passwords…There are alternatives! So why don’t we use them?
By Shehzad Mirza
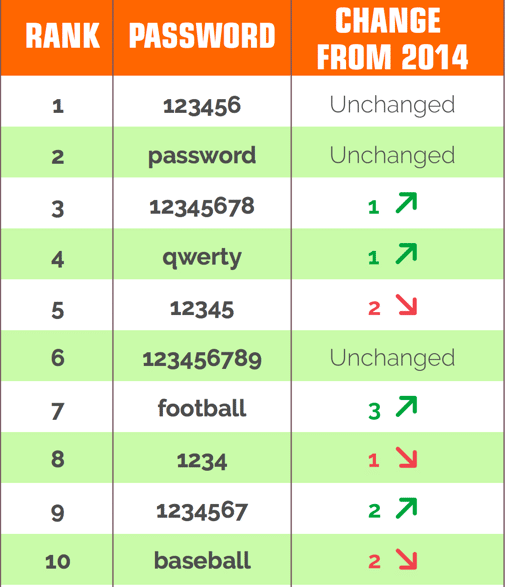
In January 2016, multiple reports were released with regards to the worst or weakest passwords in use in 2015. Based on the list below, not much has really changed from 2014, just a few passwords going up and down the list. The rest of the list isn’t any better.
The usage of passwords is nearly universal, from work to online banking to online shopping to social media. It’s an authentication mechanism that probably has the most risk associated with it, especially if the passwords on the list above are still allowed. So why are simple and weak passwords allowed? There are multiple mechanisms available to force users to use complex passwords.
Why not require an alphanumeric password? Well, one reason could be that it would just lead people to add numbers before or after a word. Only one alphanumeric password made the top 25 list of worst passwords, ‘1qaz2wsx.’ It makes the risk of password usage slightly better. So, why not add even more complexity by requiring a symbol, such as ‘$’ or ‘!.’ Getting there, but complex passwords that are alphanumeric, with a symbol, are still making the list of worst passwords. The length of the password could be increased as well, which should make it difficult (or at least time consuming) for the password to be cracked. Many organizations and websites do require this level of complexity, but accounts are still compromised. The length, strength or complexity of the password isn’t the only issue. How the password is stored or transmitted is, as well. Most account credentials are stolen from insecure databases, websites or social engineering methods (i.e. phishing). The risk of account compromises via various breaches is continuing.
So the question really becomes: Are passwords still the appropriate solution to keep user account information safe? Based on these weak passwords list, it doesn’t appear that way. So why do we still use passwords? Simply put, because it is one of the easiest mechanisms to implement. Operating systems (OS) and applications have password authentication built-in as the default. Organizations see it as an acceptable solution. OS and application authentication is primarily meant for workplace authentication for their users/employees (internal users). There are also external users which use the Internet for online shopping or banking, social media, or other personal websites. This post will primarily focus on these users. Internal user authentication is a topic for another time.
Are there things you need to do? Yes, there are.
First, if you are a developer, do NOT hard-code passwords into software or applications, especially in clear-text. In some cases, applications will transmit passwords inputted by a user. If the NSA is looking for it, then so are the bad guys.
“The NSA is also keen to find any hard-coded passwords in software or passwords that are transmitted in the clear—especially by old, legacy protocols—that can help them move laterally through a network once inside.” (NSA Hacker Chief Explains How to Keep Him Out of Your System)
Second, look to two-factor authentication. Two-factor authentication uses a combination of the following authentication methods (none of which are new):
- Something you know – password
- Something you have – token, smart card/phone
- Something you are – bio-metrics (e.g. fingerprint)
Why is this important? Let’s assume your account is compromised because someone stole your password. Well, if the authentication mechanism requires the 6 or 8 digits from a token along with your password, then you have reduced the risk of an account being compromised. Two-factor authentication is being used by companies such as PayPal, Google, Facebook, etc.. The difficulties are user awareness that two-factor authentication is available, and user reluctance to adopt measures that reduce usability. Also, supplying a security token to a customer base may not be cheap. Some tokens can cost up to $300 (or more) per person.
This is one reason why many organizations, especially where the users (or consumers) are Internet-based, are starting to focus on the use of smartphones. Smartphones or mobile phones are becoming ubiquitous in the developed world and very broadly used in the developing world; so why not use it to our advantage? [Of course there is a risk that the smartphone owner hasn’t secured their device (which is common) via a PIN or password, but that’s also a topic for another time.] There are various options that can be used.
- Free Authentication Apps – Google Authenticator (used to login to Gmail or the Google Portal, but can be used with other sites such as Drop Box or WordPress Blog), and Symantec’s VIP Access (can be used with PayPal).
- Text/SMS message – many sites are starting to use this. A text message is sent to the user’s registered phone with a string of numbers and/or text with a time limit of usage. Twitter, PayPal and Amazon provide this mechanism.
- Email message – similar to Text/SMS message.
Are these solutions suitable solutions? Possibly, but deployment is still falling short, and perhaps we lack the metrics to prove suitability and value. Are there other solutions? Most definitely, especially for employees or internal users.
The risk associated with authentication is just one of the many areas that GCA is considering. With any risk, we are looking to determine what are the best solutions, how to implement those solutions, and what issues may arise with implementation. We also want to be able to measure the impact and effectiveness of those solutions. If folks would like to provide assistance or guidance in order to address the risks associated with authentication, please feel free to comment below or send us an email [email protected].
The author, Shehzad Mirza, is the Deputy Director of Operations (NYC Office) at the Global Cyber Alliance. You can connect with Shehzad on LinkedIn.